The internet is not a public medium in North Korea; it is a government resource. The regime of Kim Jong-un keeps the country isolated from the rest of the world. So the only truth is that disseminated by the government-controlled media. The world is a dangerous place, and with all they have been told, North Koreans are grateful to be shielded from it.
It is doubtful that you will ever go to North Korea either for business or pleasure. So, this country profile will focus on the encounters that the outside world has with the state-sponsored hackers of North Korea.
Internet penetration and availability
The internet is not available for the general public in North Korea, so the country has zero internet penetration. There are some connections to the internet available for a limited number of government officials or scientific researchers. A few Web servers in the country host government website, such as the Korean Central News Agency. The government has about 30 Websites connected to the World Wide Web.
The few connections that exist to the local internet are all routed through China. The government will make a press room available for significant events intended to attract the foreign press corps; this includes a few terminals that allow internet access. It is also possible for foreigners to connect to the internet through a 3G mobile network.
What is Kwangmyong?
The country has its internet, called Kwangmyong, which has no interconnection with the internet available in other countries. Kwangmyong also works the same as the World Wide Web, except it isn’t possible to access sites outside Korea. All of the URLs on this system use the top-level domain .kp, and each is also identified by an IPv4 address, which is unique within Kwangmyong.
As Kwangmyong uses the same naming convention as the World Wide Web, the URLs are all written in Latin characters, not the Hangul alphabet used for the Korean language. This makes most URLs incomprehensible to the average user. North Koreans prefer to access sites by typing the IP address into the address bar instead of an alphabetical URL. This loses many of the marketing advantages that Western eCommerce operators deploy with their choice of domain name.
As IP addresses are difficult to remember, search engines and bookmarking are essential mechanisms for finding or revisiting sites on Kwangmyong. However, these practices make TV or radio advert tie-ins to sites challenging to accomplish.
There are no connections between Kwangmyong and the internet. To keep an apparent division between the two systems, the government of North Korea ensures that any building from which it is possible to connect to the internet does not have any devices within it that can connect to Kwangmyong.
Internet speeds in North Korea
As North Korea is a closed society, it is challenging to get information on its internet performance. In fact, given that very few people in North Korea have access to the global system, it is almost impossible to track down anyone who has used the internet there and is prepared to talk. Therefore, it is also practically impossible to get information about the performance of Kwangmyong.
Akamai performed the last international internet speed comparison that included North Korea in June 2016. At that time, the average speed of the internet worldwide was calculated at 5.6 Mbps. The survey reported average speeds in 170 countries.
North Korea, with an average speed of 2 Mbps, didn’t come last. It ranked 134th on the list. However, it is not clear whether that speed was measured for the actual internet or Kwangmyong.
In that report, the average internet speed for South Korea put it in the number one slot with 26.7 Mbps. For comparison, the report recorded an average speed of 14.2 Mbps in the USA.
Digital awareness
It is challenging to get a computer in North Korea. Few stores stock them, and a potential buyer has to get clearance from the police before they are even allowed to browse. This permission is only granted after a home visit from the security service and lengthy questioning of all household members. There are about 200,000 homes with a computer in North Korea.
Kwangmyong is a dial-up service. To get access from home, the user would need to get a higher security clearance which involves more assessment visits and interviews. Almost all home computers connected to Kwangmyong are in the capital, Pyongyang.
More recently, it has become possible to connect to Kwangmyong through a mobile phone or tablet. There are about 4.5 million mobile devices in North Korea.
Access to Kwangmyong is more commonly affected through computer rooms in university libraries or large factories. There are several cybercafes allowed around the country that would enable access to Kwangmyong by buying a time-based ticket. However, the cost of these tickets is very high and beyond the means of the average citizen.
The Kwangmyong network’s services include access to chat rooms, but the national equivalent to Facebook was shut down in 2006. However, a regional message board system is available, which allows academics to access a chat facility. There is also a video chat system open to the general public for person-to-person video calls. This was launched in 2010 and is called Raekwon. Television news journalists often use this system to post reports from around the country.
Dating chat is allowed on Kwangmyong, and there are also some video games available online, such as Korean Chess.
Online anonymity
There is no online anonymity in North Korea because the government provides all services, and all usage is tracked.
An email system is included in the standard services of Kwangmyong, and there is one state-run search engine available. Access to the site on Kwangmyong is performed through a normal state-approved browser. As all activities on Kwangmyong are monitored, and access is regarded as a privilege for the few, the idea of sending spam emails or creating Web hacks on Kwangmyong is unheard of.
Access to privacy tools
There are no VPNs in North Korea. So if you are a foreigner and have a VPN subscription at home, it will do you no good when you get to North Korea. First, you won’t be able to connect to the actual internet. Second, if you manage to obtain permission to access Kwangmyong, your VPN client won’t be able to get through to any of the international servers of your provider.
North Koreans cannot access VPN websites and so couldn’t take out a VPN subscription even if they had a bank account that could send an international payment. No VPN services are operating on Kwangmyong.
Burner phones and temporary webmail accounts are not available in North Korea. However, registering for any service on Kwangmyong means that you can be identified in all of your actions online.
Surprisingly, there is some Tor activity emanating from North Korea. However, as this activity is registered on the internet rather than Kwangmyong, these protected connections are probably for hacking research. The graph below shows Tor connections from North Korea. It is the definitive record generated by the Tor Project spanning from August 2020 to August 2021.
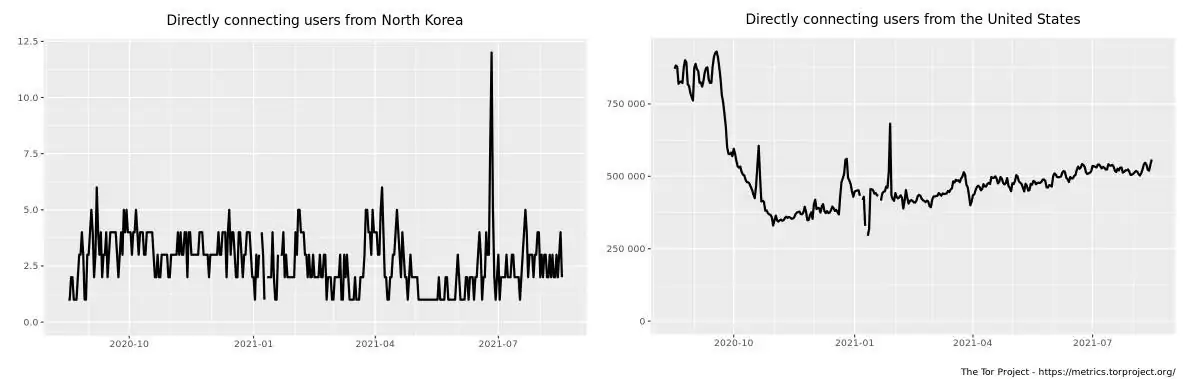
This graph shows the number of users on the Tor network per day in North Korea. There is always one person connected each day during the year. The maximum number of users on any day was 6, except one day at the end of June 2021, when 12 people were connected.
By contrast, the adjacent graph shows the number of users in the USA. Apart from a very active period in September 2020, the range of daily US users of Tor is between 275,000 and 550,000.
Cybercrime: prevalence and attack types
Domestically, there is no cybercrime in North Korea. Foreign hackers can’t get into Kwangmyong. Anonymous claimed to have broken into the network in 2013, but they could not provide evidence or repeat the achievement with witnesses watching for verification. No one within North Korea would ever perform any cybercrimes on Kwangmyong.
Hacking from within North Korea out to the rest of the world is a different story. North Korea has a very active squadron of hackers entirely controlled by the government and is among the few people in the country who ever access the actual internet.
The government intelligence agency organizes all hackers in North Korea into an organization called the Lazarus Group. Although the leading players in this group started as independent hackers, they have since come under the control of the government.
Whois Team also knows the state-controlled team, Guardians of Peace, Hidden Cobra, ZINC, God’s Apostles, and God’s Discipline. The group implements attacks for intelligence and disruption rather than for financial gain, although they make money from their attacks as a side-benefit.
One of the regular activities of the Lazarus Group is to launch DDoS attacks against targets in South Korea and the USA. This campaign started in 2009 but has become less frequent since 2012 when the group focused on implementing advanced persistent threats (APTs). In an APT, the hacker gains entry and manually explores the target network, using hacking tools to automate research and brute force credentials cracking.
APT hackers institute routines to periodically alter or delete log files to hide records of their activities. However, as SIEM services and intrusion detection systems become more widely used by the world’s business communities and governments, the opportunities for APT activity are reducing.
The Lazarus Group has two specialist divisions that perform services for the team and also for commissioning associates. The first of these is BlueNorOff, aka APT38, and Stardust Chollima. This team moves money internationally between bank accounts by manipulating SWIFT records. This is for theft and also to hide the movements of the group’s earnings. The other unit is called AndAriel, which is also known as Silent Chollima. The team specializes in APTs in South Korea.
The biggest heist by BlueNorOff was the theft of more than $100 million from the Bangladesh Bank in 2016. The whole scheme was to take $1 billion, but the operation was discovered and blocked once the first two tranches had been completed.
In 2014, the Lazarus Group, operating under the name the Guardians of Peace, broke into the system of Sony Pictures and stole a large amount of personally identifiable information (PII). This attack was inspired by the anger of North Korea’s leader, Kim Jong-un, who was incensed by the upcoming release of the film The Interview. The plot of that film was based on a fictional attempt to assassinate the President of North Korea, and Kim Jong-un wanted to prevent the movie’s release.
The data theft from Sony Pictures aimed to blackmail the production company into canceling the release of The Interview by periodically releasing tranches of the stolen data on the Dark Web, where other hackers could use it. Instead, the company relented and shelved the release of the film.
One of the most famous ransomware attacks in history, WannaCry, launched in 2017, blamed the Lazarus Group. However, the attribution has never been conclusive, with some analysis blaming hacker groups in Hong Kong or Southern China.
More recently, the group attempted to break into the system of AstraZeneca to steal its Covid-19 vaccine research. However, the attack was unsuccessful, and the group is believed to have targeted other major pharmaceutical labs simultaneously.
The Lazarus Group is still active today. In August 2021, the team was revealed to have been active, APT-style within a South Korean media group system.
